File Replication Service Problems
Situation:
Your Active Directory environment seems to be working fine. Yet you discover that policies are not always being executed. Sometimes they are, sometimes they're not.
When you check AD replication everything is ok and new objects are replicated to all of the domain controllers. But when you check the Sysvol, one of your DCs seems to be out of date.
After testing Sysvol replication (by adding a file to the sysvol on a good DC and forcing replication to the outdated DC) you discover that this domain controller never receives group policy updates.
Problem:
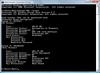
When you check the Event Viewer on the problem DC, you see the following error message:
Event Id 13561: The File Replication Service has detected that the replica set "Sysvol" is in JRNL_WRAP_ERROR.
A replica set hits JRNL_WRAP_ERROR when the record it is trying to read from the NTFS USN journal is not found. This can occur because of one of the following reasons: ...
Solution:
You will have to remove the server from the Replica Set and then add it again. This will cause the DC to replicate the entire Sysvol again. To accomplish this, do the following:
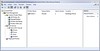
1. Start Registry Editor.
2. Find the following key: HKEY_LOCAL_MACHINE\System \CurrentControlSet\Services\Ntfrs\Parameters
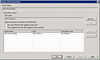
3. Add a new Dword value: Enable Journal Wrap Automatic Restore
4. Set the value to 1.
5. Wait for the Sysvol to get replicated. During this time you will see the following events in the Event Viewer:
13560: FRS is deleting the computer from the replica set.
13553: FRS has added the computer to the replica set.
13516: FRS is no longer preventing the computer from becoming a DC.
At that moment everything should be fine again!
Remark:
Do not forget to change the value of the Journal Wrap Automatic Restore back to 0!