Bitlocker Drive Encryption (without TPM)
Most of you have probably already heard about Bitlocker. But for those of you who don't know it, here's a short overview.
Bitlocker is a data protection feature available in Windows Vista and Longhorn Server. It is implemented to address the threats of data theft or exposure from lost or stolen PCs.
Bitlocker prevents a thief who boots another operating system or runs a software hacking tool from breaking Windows Vista file and system protections or performing offline viewing of the files stored on the protected drive.
Bitlocker enhances data protection by bringing together two major sub-functions: full drive encryption and the integrity checking of early boot components:
- Drive encryption protects data by preventing unauthorized users from breaking Windows file and system protection on lost or stolen computers. This protection is achieved by encrypting the entire Windows volume. With Bitlocker all user and system files are encrypted including the swap and hibernation files.
- Integrity checking the early boot components helps to ensure that data decryption is performed only if those components appear unmolested and that the encrypted drive is located in the original computer.
The feature ideally uses a Trusted Platform Module (TPM 1.2) to protect user data and to ensure that the PC has not been tampered with while the system was offline.
A TPM is a microchip designed to provide basic security-related functions, primarily involving encryption keys.
Now what if you do not have a TPM, but you would like to use Bitlocker Drive Encryption?
No problem, BDE is supported on machines without TPM. The only tricky part is that you cannot enable it using the GUI. In Control Panel (where you would normally enable Bitlocker), you'll see the following:
So, how do you enable bitlocker then?
You will have to use manage-bde, a cscript tool that works with Bitlocker through the WMI interface.
This is what you do:
- Open a Command Prompt as administrator! (Rightclick the cmd shortcut in the Start menu and choose "Run as administrator".)
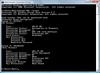
- cscript manage-bde.wsf -on C: -sk h: -rp -rk f:
Command Explanation -on C: Enable BDE on drive C: -sk h: Create a startup key and save it on drive h:
Drive h: will normally be a USB key-rp Create a recovery password -rk f: Create a recovery key and save it on drive f:
Drive f: can be a USB key, hard drive, network drive
- Save the numerical recovery password in a save place!
- Insert your USB drive.
- Restart your computer for a hardware test.
- Use manage-bde -status to check whether the test was successful. If it was, encryption will begin. You can use the same command to keep track of the encryption progress.